Vulnerability Assessment
Scanning computer hosts, servers, network devices, and websites for known vulnerabilities and backdoors.
* In-depth analysis, adjustment and elimination of misjudgment.
* Assess the risk level of the environment and provide suggestion.
* Ensure that device security is maintained at its best.
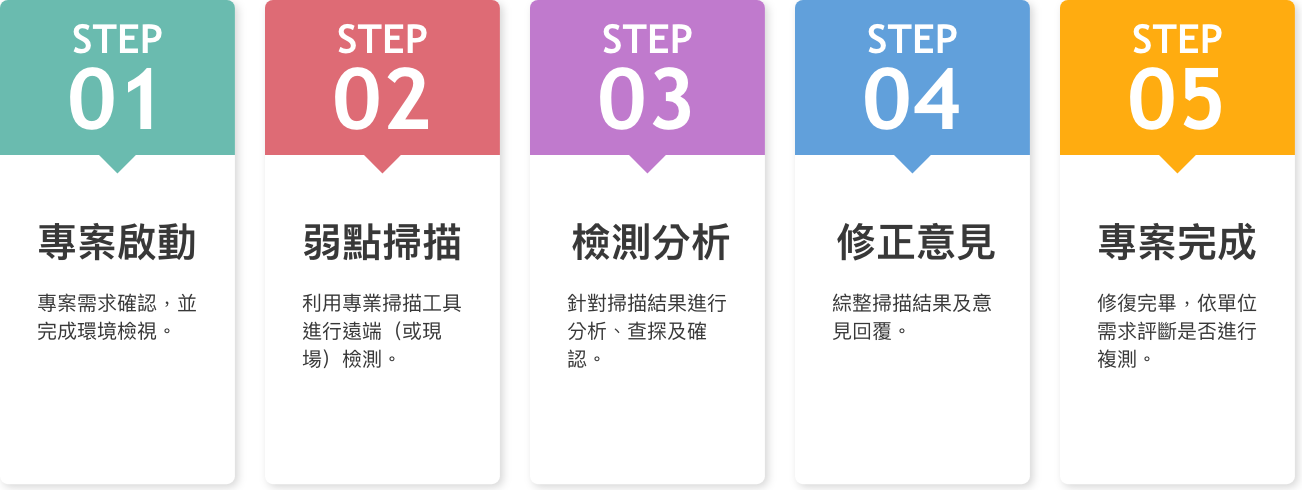
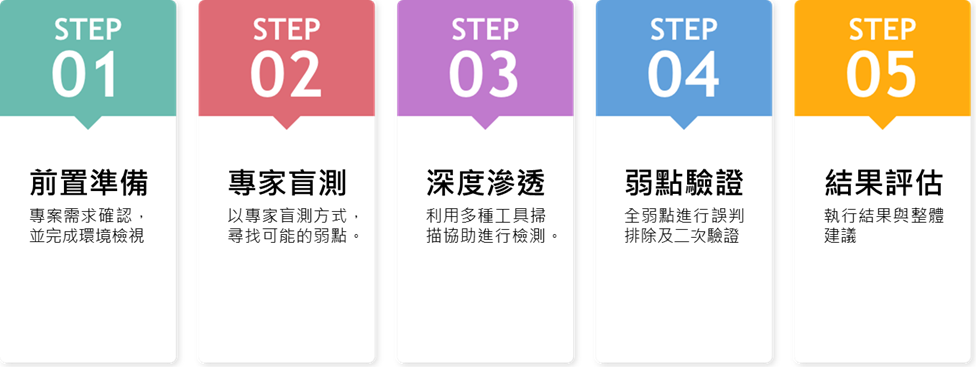
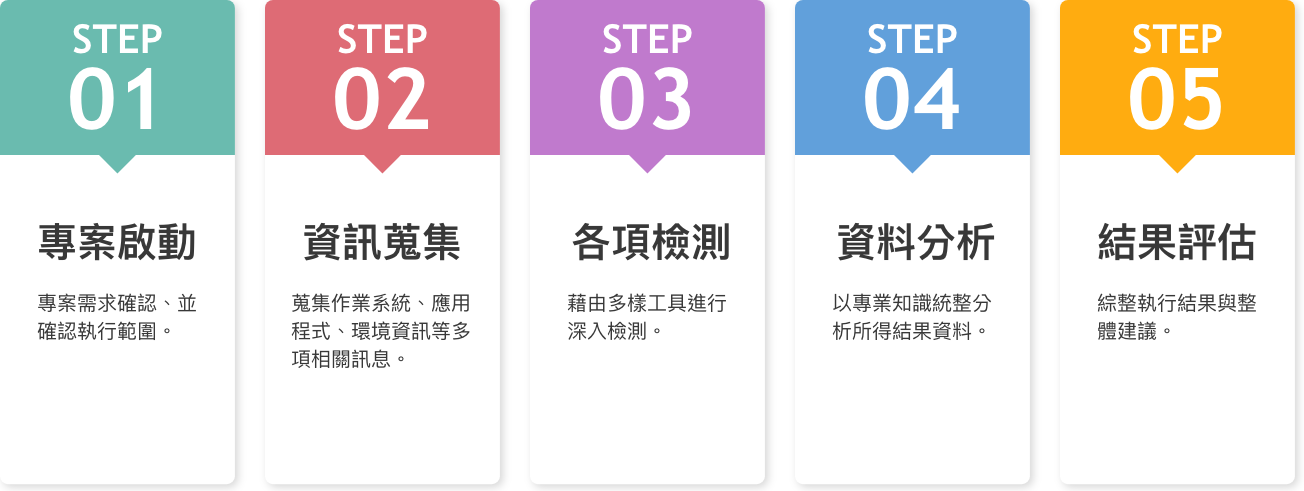
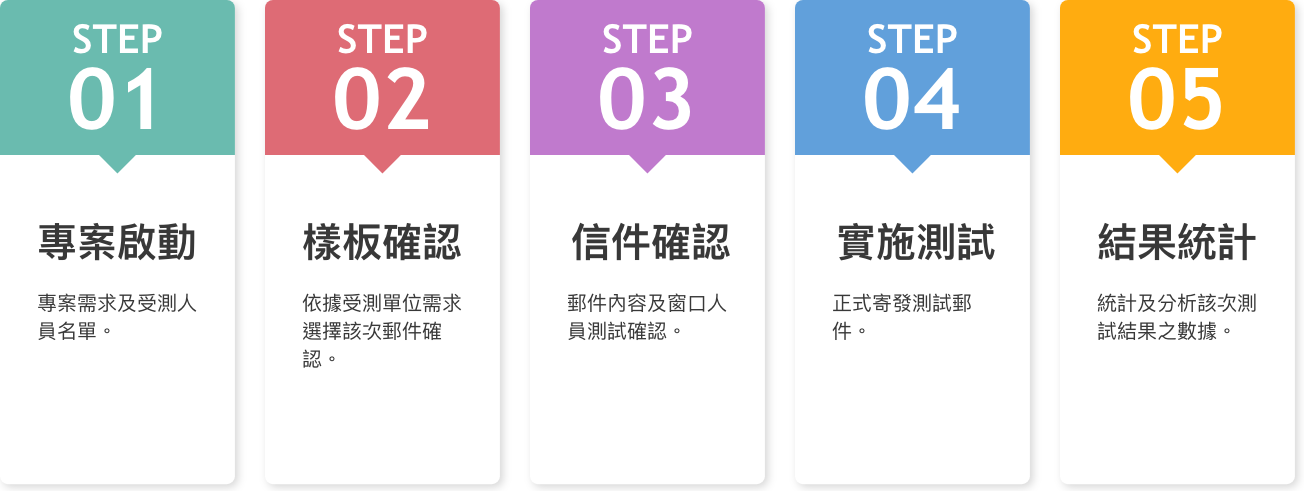
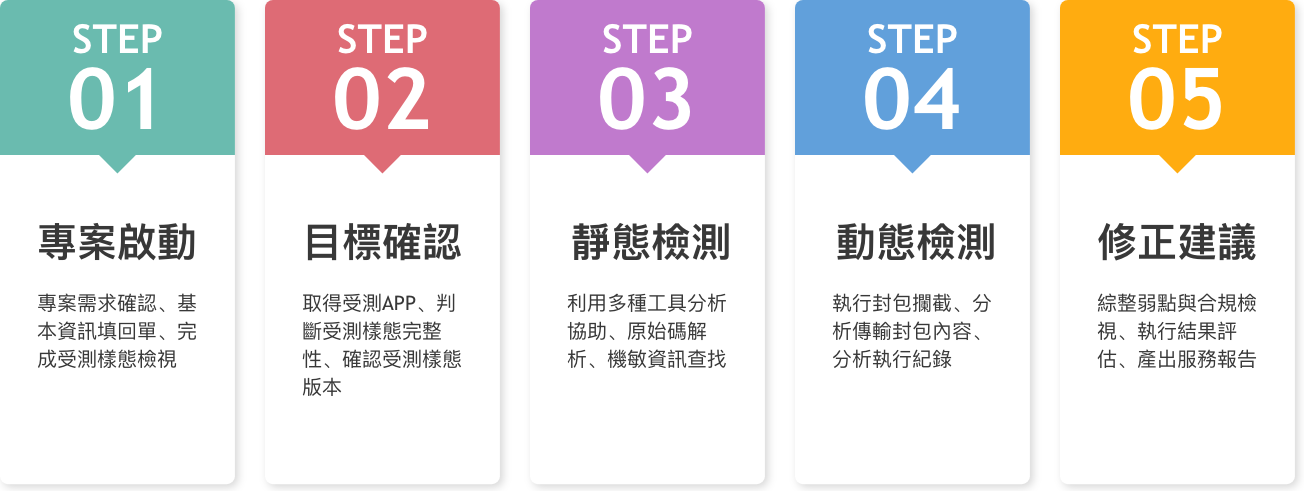
Flowchart